
Static Application Security Testing (SAST) is a white-box testing approach that analyzes an application's source code, bytecode, or binary code without actually running the application. This method focuses on examining the internal structure of the code to detect vulnerabilities early in the development lifecycle. SAST is widely valued for helping developers identify and fix potential security risks before they make it into production, thus reducing the likelihood of costly vulnerabilities down the line.
SAST is most effective when used in the early stages of development as part of a "shift-left" security strategy, which emphasizes embedding security earlier in the development lifecycle. This approach reduces the time and cost of fixing vulnerabilities by catching them before they reach production.
Dynamic Application Security Testing (DAST) is a black-box testing approach that evaluates the security of an application in a running environment. Unlike SAST, DAST does not require access to the source code; instead, it simulates real-world attack scenarios to identify vulnerabilities in a live, operational application. This approach is ideal for finding issues related to runtime behavior, such as authentication, session management, and API misconfigurations.
DAST is particularly useful in testing and production environments, where applications are live and fully operational. It’s highly effective for finding security gaps that only appear when the application is deployed and interacting with end users.
| Factor | SAST | DAST |
|---|---|---|
| Testing Stage | Early (during development) | Later (in staging or production) |
| Type of Access | Requires source or binary code access | No code access required |
| Detection | Static vulnerabilities (e.g., code flaws) | Runtime vulnerabilities (e.g., logic flaws) |
| Integration | CI/CD, DevSecOps, IDEs | Can run alongside production and testing |
| Compliance Support | Supports compliance (PCI-DSS, ISO) | Suitable for pen-testing requirements |
| Primary Use Case | Code quality and early flaw detection | Behavioral analysis and runtime testing |
Combining Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) creates a robust, holistic security approach. This combination covers both code vulnerabilities and runtime issues, providing broader protection. SAST and DAST together allow organizations to "shift left" by identifying security flaws early in development and "shift right" by monitoring applications continuously in production. This dual approach improves security by capturing coding errors and behavioral flaws that only appear in a live environment.
This combined strategy supports compliance standards and fosters long-term resilience, making it ideal for companies implementing DevSecOps practices to integrate security at every stage of the development lifecycle. With tools like Trixus for real-time testing and reporting, organizations can ensure robust coverage and compliance across their applications.
Choosing the right security partner is not about running tools — it is about understanding how real attackers think and how real systems fail in production. Krya Solutions focuses on practical, impact-driven application security, not checklist-based scanning.
Unlike generic security vendors, Krya Solutions approaches SAST and DAST from an attacker's path and developer's reality, ensuring findings are relevant, exploitable, and actionable.
 Clear vulnerable code paths
Clear vulnerable code paths Root cause analysis
Root cause analysis Developer-friendly remediation guidance
Developer-friendly remediation guidance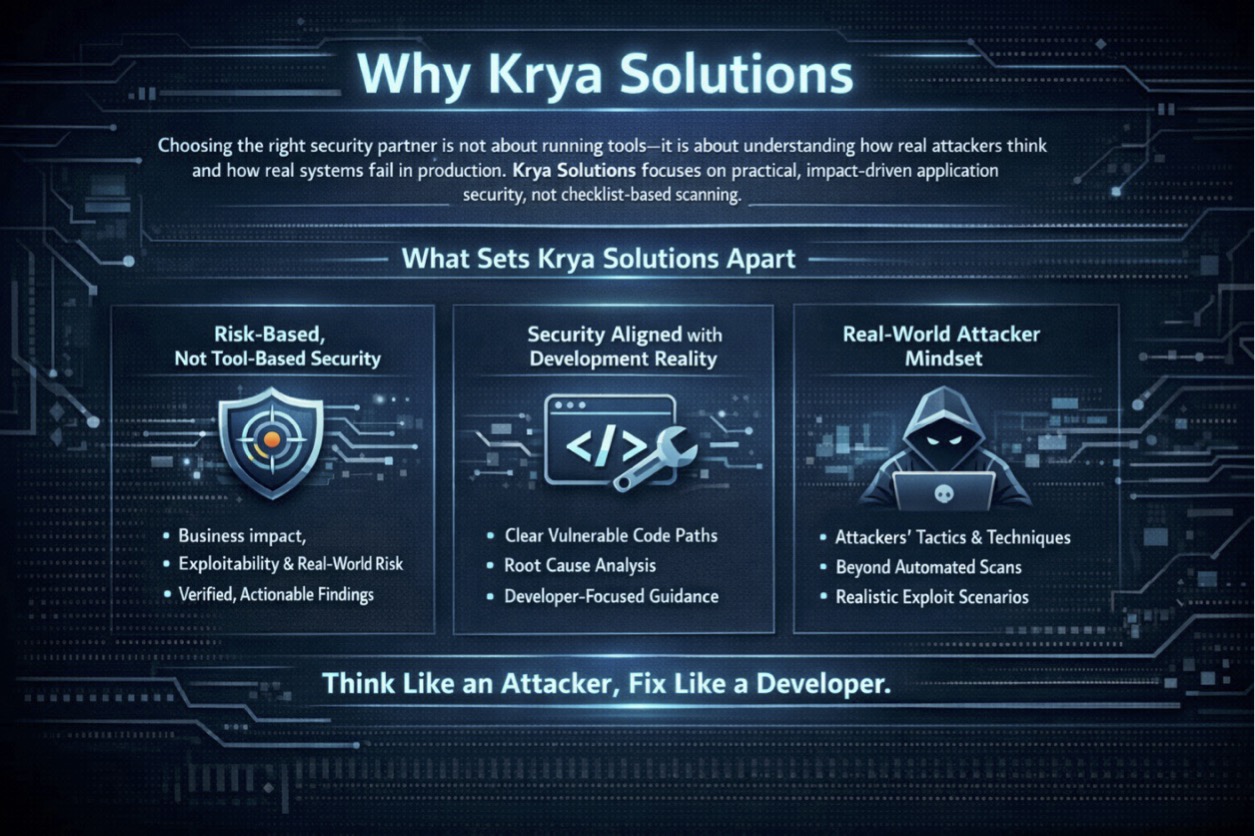
Contact us to learn more. Call +91 44 6669 2727 or Email ks-info@kryasolutions.com
Download Brochure