
Zero Trust is especially relevant in today's world of remote work, cloud computing, and BYOD (Bring Your Own Device) environments. It helps:
 Reduce the attack surface
Reduce the attack surface
 Improve compliance
Improve compliance
 Strengthen overall security posture
Strengthen overall security posture
However, achieving a true state of Zero Trust is not straightforward. Organizations often encounter challenges such as legacy systems, budget constraints, and internal resistance.
Traditional Security
 Trusts internal network
Trusts internal network
 Static perimeters
Static perimeters
 Coarse-grained access
Coarse-grained access
 Reactive monitoring
Reactive monitoring
Zero Trust Security
 Trusts no one, verifies all
Trusts no one, verifies all
 Dynamic and adaptive
Dynamic and adaptive
 Fine-grained, least privilege access
Fine-grained, least privilege access
 Proactive threat containment
Proactive threat containment
As organizations move to the cloud, embrace remote work, and face increasingly sophisticated cyber threats, the old "castle and moat" model just doesn't cut it. Zero Trust is designed for a borderless, dynamic environment where security must adapt in real time.
 The CISO sets the vision and ensures alignment with business goals.
The CISO sets the vision and ensures alignment with business goals.
 The Practitioner translates that vision into actionable Zero Trust strategies.
The Practitioner translates that vision into actionable Zero Trust strategies.
 Implementors bring that vision to life through technology and operations.
Implementors bring that vision to life through technology and operations.
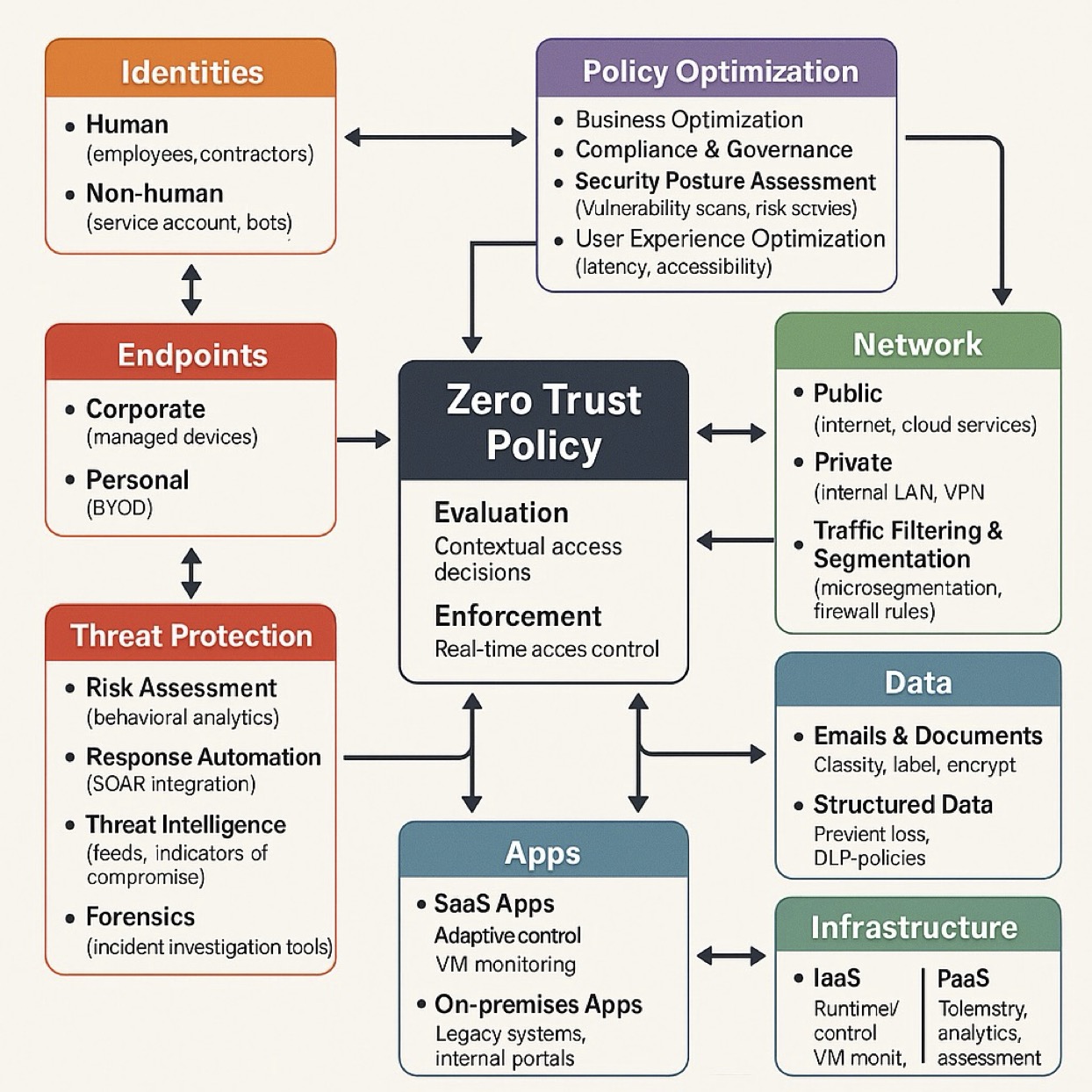
Designing a Zero Trust architecture aligned with the organization’s security environment involves changes to core system components across seven areas: user identity, devices, network and environment, applications and workloads, data, visibility and analytics, and automation and orchestration.
Ensuring successful implementation requires understanding the current security tools and infrastructure, critical data and systems, risk tolerance, regulatory commitments, and business goals. Conducting threat modelling and product security testing can help determine where Zero Trust principles would be most impactful.
Layer
 Identity and Access Management (IAM)
Identity and Access Management (IAM)
 Device Security
Device Security
 Network Segmentation
Network Segmentation
 Application Security
Application Security
 Data Security
Data Security
 Visibility, Analytics, Automation & Orchestration
Visibility, Analytics, Automation & Orchestration
Technology/Function
 IdP, MFA, SSO, SCIM, RBAC
IdP, MFA, SSO, SCIM, RBAC
 MDM, device compliance, endpoint health
MDM, device compliance, endpoint health
 Micro segmentation, encrypted tunnels, east-west firewalls
Micro segmentation, encrypted tunnels, east-west firewalls
 Reverse proxy, CASB, SDP/ZTNA gateways
Reverse proxy, CASB, SDP/ZTNA gateways
 DLP, DRM, tokenization, audit
DLP, DRM, tokenization, audit
 SIEM, XDR, SOAR, UBA , policy engines, policy enforcement.
SIEM, XDR, SOAR, UBA , policy engines, policy enforcement.
1. Baseline Assessment
 Identify crown jewels (data, apps, identities).
Identify crown jewels (data, apps, identities).
 Perform gap analysis on existing controls.
Perform gap analysis on existing controls.
2. Quick Wins
 Enforce MFA for all users.
Enforce MFA for all users.
 Enable device compliance checks.
Enable device compliance checks.
 Audit excessive permissions.
Audit excessive permissions.
3. Architecture Design
 Define trust boundaries and access workflows.
Define trust boundaries and access workflows.
 Segment per identity, not just IP or subnet.
Segment per identity, not just IP or subnet.
4. Toolchain Integration
 SIEM + UEBA + EDR + CASB into a unified response pipeline.
SIEM + UEBA + EDR + CASB into a unified response pipeline.
5. Policy-as-Code
 Automate security controls via CI/CD and IaC (e.g., Terraform, Ansible).
Automate security controls via CI/CD and IaC (e.g., Terraform, Ansible).
 Cultural and organizational resistance
Cultural and organizational resistance
 Complexity in legacy environments
Complexity in legacy environments
 Need for cross-functional collaboration (IT, security, networking)
Need for cross-functional collaboration (IT, security, networking)
 Initial costs of technology integration
Initial costs of technology integration
With that said, Zero Trust isn’t a product – it's a comprehensive security strategy built over time. It requires cross-disciplinary collaboration between security, IT, and dev teams. With proper design, it enables secure digital transformation that is resilient, scalable, and future-ready.
Krya Solution's strategy guide assesses these intricacies from both the CISO and practitioner perspectives, providing actionable insights for overcoming roadblocks to successfully implement Zero Trust at scale.
Contact us to learn more. Call +91 44 6669 2727 or Email ks-info@kryasolutions.com
Download Brochure